Configure AD FS
To configure AD FS for integration with Keycloak, we need to add a new Relying Party Trust and set up claim issuance policy.
Add Relying Party Trust
Open the AD FS Management console on the Windows Server and follow the steps below:
- Right-click on
Trust relationshipsand selectAdd Relying Party Trusts...from the context menu. - Select
Claims awareand clickStart. - Import data about the relying party using URL or manually via file by clicking browse and click
Next. You can find the SAML 2.0 service provider metadata URL in the Keycloak configuration. - Enter the
Display nameof the new relying party and clickNext. - Adjust the
Access control Policyto limit users from using the new relying party and clickNext. - Review all settings and click
Next. - Keep the
Configure claims issuance policy for this applicationcheckbox checked and clickCloseto add the new relying party trust.
The new relying party trust is now added to the list of relying party trusts. Users can authenticate using the new relying party trust, however, no user attributes are sent to the service provider. For that, we need to set up claim mapping.
Setup claim issuance policy
Open the AD FS Management console on the Windows Server. In the list of Relying Party Trusts right-click on the relying party and from the context menu select Edit claim Issuance Policy... to open the editor. Configure the following rules:
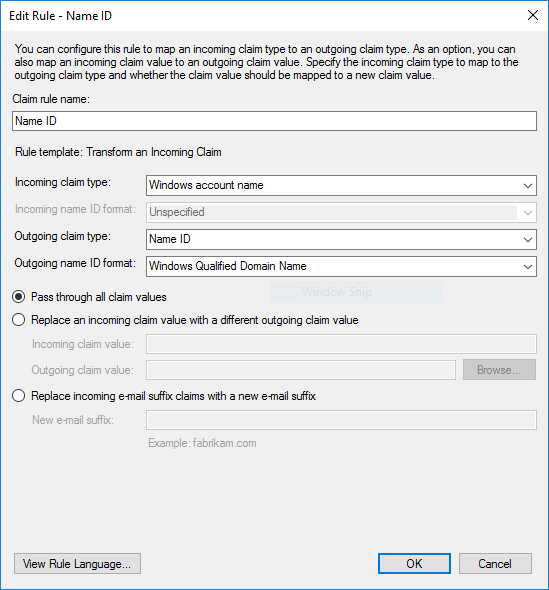
Name ID
- Click on
Add Rule...to open theAdd Transform Claim Rule Wizard. - Select
Transform an Incoming Claimand clickNext. - Enter the
Claim rule nameasName ID. - Select
Windows Account Nameas theIncoming claim typeandName IDas theOutgoing claim type. - Select
Outgoing name ID formatasWindows Qualified Domain Nameand clickFinish.
This rule will provide claims about the user's name in the format username/domain.
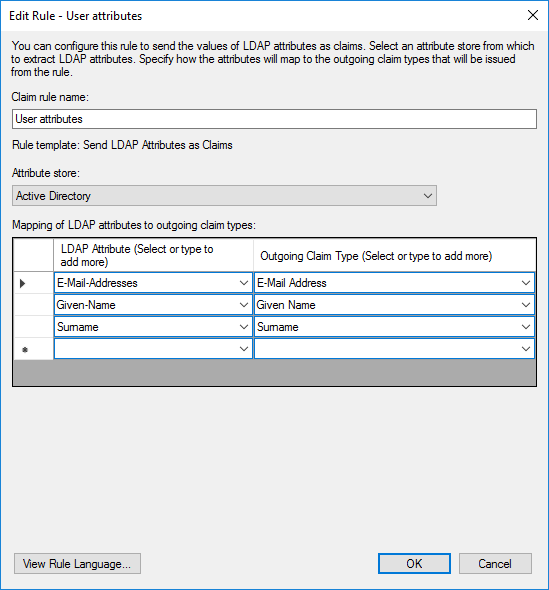
User attributes
- Click on
Add Rule...to open theAdd Transform Claim Rule Wizard. - Select
Send LDAP Attributes as Claimsand clickNext. - Enter the
Claim rule nameasUser attributes. - Select
Active Directoryas theAttribute store. - Select the
LDAP AttributeasE-Mail-Addressesand theOutgoing Claim TypeasE-Mail Address. - Select the
LDAP AttributeasGiven-Nameand theOutgoing Claim TypeasGiven Name. - Select the
LDAP AttributeasSurnameand theOutgoing Claim TypeasSurname. - Click
Finish.
This rule will provide claims about the user's email address, given name, and surname from the Active Directory data.
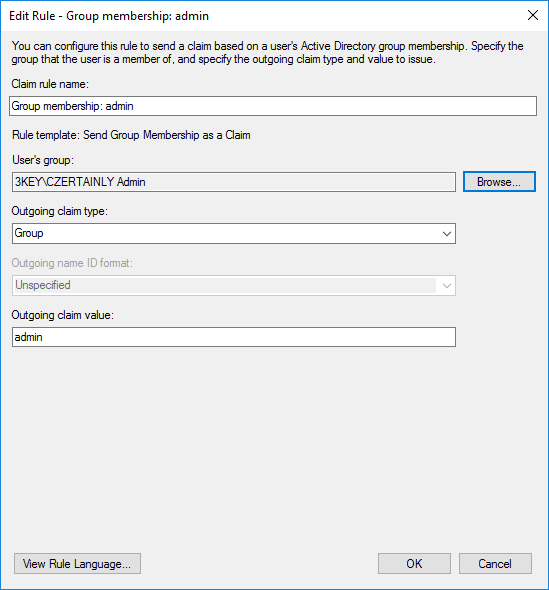
Group membership
- Click on
Add Rule...to open theAdd Transform Claim Rule Wizard. - Select
Send Group Membership as a Claimand clickNext. - Enter the
Claim rule nameasGroup membership: admin. Change the name according to the group you want to send. - Select user's group using
Browse...button. - Select
Groupas theOutgoing claim type. - Select the
Outgoing claim valueas the the associated name of the role in the CZERTAINLY platform, for exampleadmin. - Click
Finish.
This rule will provide claims about the user's group membership in the format of the group name.
The group membership rule will provide claims about the user's group membership only in case the user is a member of the selected group. If you want to provide claims about multiple groups, you need to create a separate rule for each group. The group name should match the role name in the CZERTAINLY platform, or it will be created as a new role, depending on the platform configuration.
PowerShell configuration
You can use PowerShell to automate the configuration of the AD FS relying party trust and claim issuance policy. The following script will add a new relying party trust and configure claim issuance policy for the new relying party trust. Change the $metadataUrl, $relyingPartyName, and $accessControlPolicy variables to match your environment.
# Add new relying party trust
$metadataUrl = "https://keycloak.example.com/realms/CZERTAINLY/broker/adfs-idp-alias/endpoint/descriptor"
$relyingPartyName = "CZERTAINLY"
$accessControlPolicyName = "Permit everyone"
$relyingPartyTrust = Add-AdfsRelyingPartyTrust -MetadataUrl $metadataUrl -Name $relyingPartyName -AccessControlPolicyName $accessControlPolicy
# Get the group SID
$groupSid = (Get-ADGroup -Filter {Name -eq "Administrators"}).SID.Value
# Configure claim issuance policy
$stringClaimRule = @'
@RuleTemplate = "MapClaims"
@RuleName = "Name ID"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname"]
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName");
@RuleTemplate = "LdapClaims"
@RuleName = "User attributes"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress", "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname", "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname"), query = ";mail,givenName,sn;{0}", param = c.Value);
@RuleTemplate = "EmitGroupClaims"
@RuleName = "Group membership: admin"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value == "$groupSid", Issuer == "AD AUTHORITY"]
=> issue(Type = "http://schemas.xmlsoap.org/claims/Group", Value = "admin", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, ValueType = c.ValueType);
'@
$stringClaimRule = $stringClaimRule.Replace('$groupSid', $groupSid)
$issuancerules = New-AdfsClaimRuleSet -ClaimRule $stringClaimRule
# Get relying party trust
$relyingparty = Get-ADFSRelyingPartyTrust -Name $relyingPartyName
# Set claim issuance policy
Set-AdfsRelyingPartyTrust -TargetName $relyingParty.Name -IssuanceTransformRules $issuancerules.ClaimRulesString